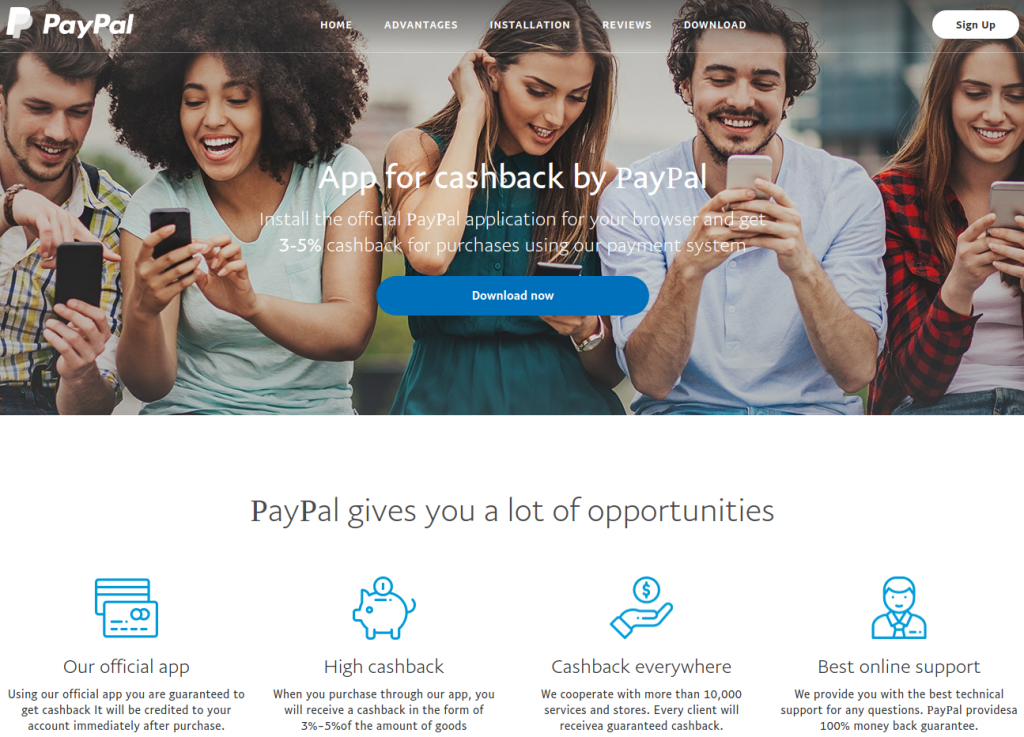
The providers of this file encryption malware seem to be testing multiple distribution channels as a payload from the Exploit Kit of RIG (EK) has lately been observed. Worship with cashback. Nemty’s recent occurrence was noted on a fake PayPal website which promises to return 3-5% of the payments produced through the payment scheme.
Various clues point out that the page’s fraudulent nature is also flagged as hazardous by main browsers, but users can still go for this trick and download and run malware conveniently known as cashback.exe. Security investigator nao sec has discovered a new distribution channel Nemty and used the malware to run the AnyRun test environment and to track its activities on an infected system. The automated assessment revealed that the ransomware took about seven minutes to encrypt the documents on the victim’s host. This may, however, vary from one scheme to another. Fortunately, most common antivirus products on the market detect the malicious executable. A scan of VirusTotal shows that 36 of the 68 antivirus engines are identified.
Attack homoglyph
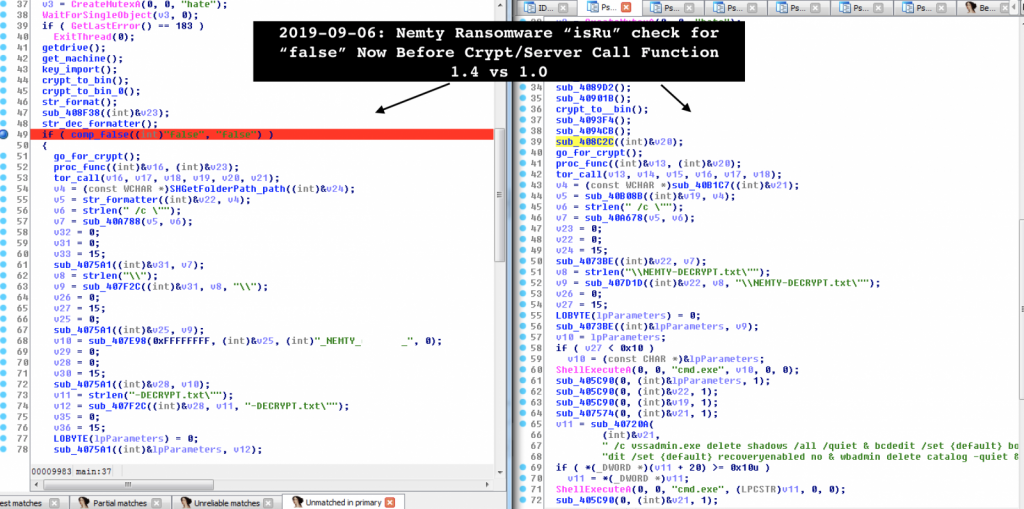
At first glance, the website appears to be real as cyber criminals used the images and structure on the initial page. Cyber criminals also use homograph names for connections to multiple parts of the site (Help and Contact, Fees, Security, Apps & Shop) to add to their disappointment. The crooks have accomplished this by using Unicode characters from distinct alphabets in the domain name. To differentiate between them, browsers convert them into Punycode automatically. In this situation, what appears on paypal.com in Unicode translates on Punycode to’ xn—ayal-f6dc.com.’ Vitali Kremez, a security investigator, analyzed this variant of Nemty Ransomware, observed that version 1.4 now includes minor bug fixes. One thing the investigator noted was that the “isRU” check, which determines whether the infected computer has been altered in Russia, Belarus, Kazakhstan, Tajikistan or Ukraine. In the recent version the malware does not travel with the file encryption feature if the check outcome is positive, the investigator informed.
Vitali Kremez However, computers outside these nations are a target and will encrypt their files and delete their shadow copies. Nemty ransomware has been on cybercriminal forums for a while, but came out on the infosec community radar in late August, when safety investigator Vitali Kremez released information of his assessment. In the code texts and references, the specialist noticed the malware. They are testing showed that the restitution requirement is 0.09981 BTC, or $1,000, which is hosting the payment portal for anonymity on the Tor network. Another safety investigator, Mol69, saw Nemty being distributed via RIG EK at the end of August, a strange decision likely as exploit kits are on the verge of extinction, as they targeted products on their death bed: the Internet Explorer and the Flash Player. According to Yelisey Boguslavskiy of Advanced Intelligence, Nemty was greeted at the ordinary cybercriminal forum in that society with “extreme skepticism and aggression.” This can also affect its achievement, as Sodinokibi ransomware presently enjoys nothing. Credit:BleepingComputer